In this article you will read about,
- how confidential computing ensures confidentiality,
- what the possible applications are,
- and how confidential computing replaces expensive hardware security modules.
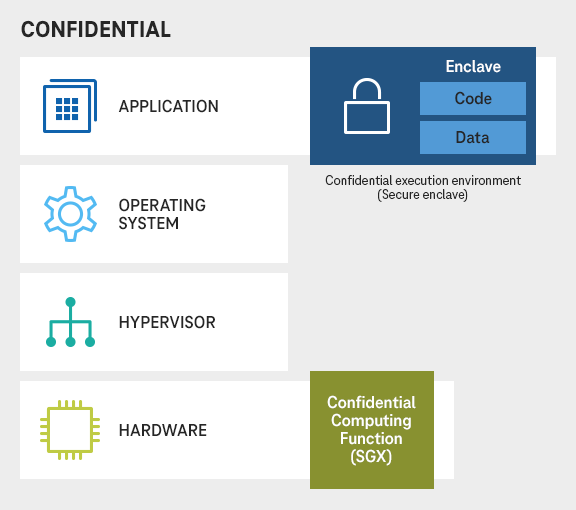
Confidential computing is a technology that ensures the security and confidentiality of sensitive data processing in cloud environments. Confidential computing adds another security component that, among other things, effectively prevents the provider from gaining access to the data. This is a necessary security standard, especially in regulated environments such as the healthcare industry. Health insurance companies, for example, use the technology to implement secure digital identities for their customers.